
Insured but Not Secure:
The Reality of Cyber Insurance
Discover why relying solely on cyber insurance leaves you vulnerable to breaches.
Secure Your Complimentary Cyber Insurance Risk Evaluation Today! We'll even help you fill out the forms!
Your Business Could Be At Risk:
Is Your Business Ready For The DoD’s CMMC Deadline?
Get A FREE 10-Point CMMC Action Plan With A Certified Assessor To Find Out Now:

What is Cyber Security Insurance?
Cyber insurance can help a business cover financial damages brought on by data breaches and other cyber catastrophes after the event. Having insurance can only provide post-incident financial support, it does NOT proactively protect your systems from cyber-attacks.
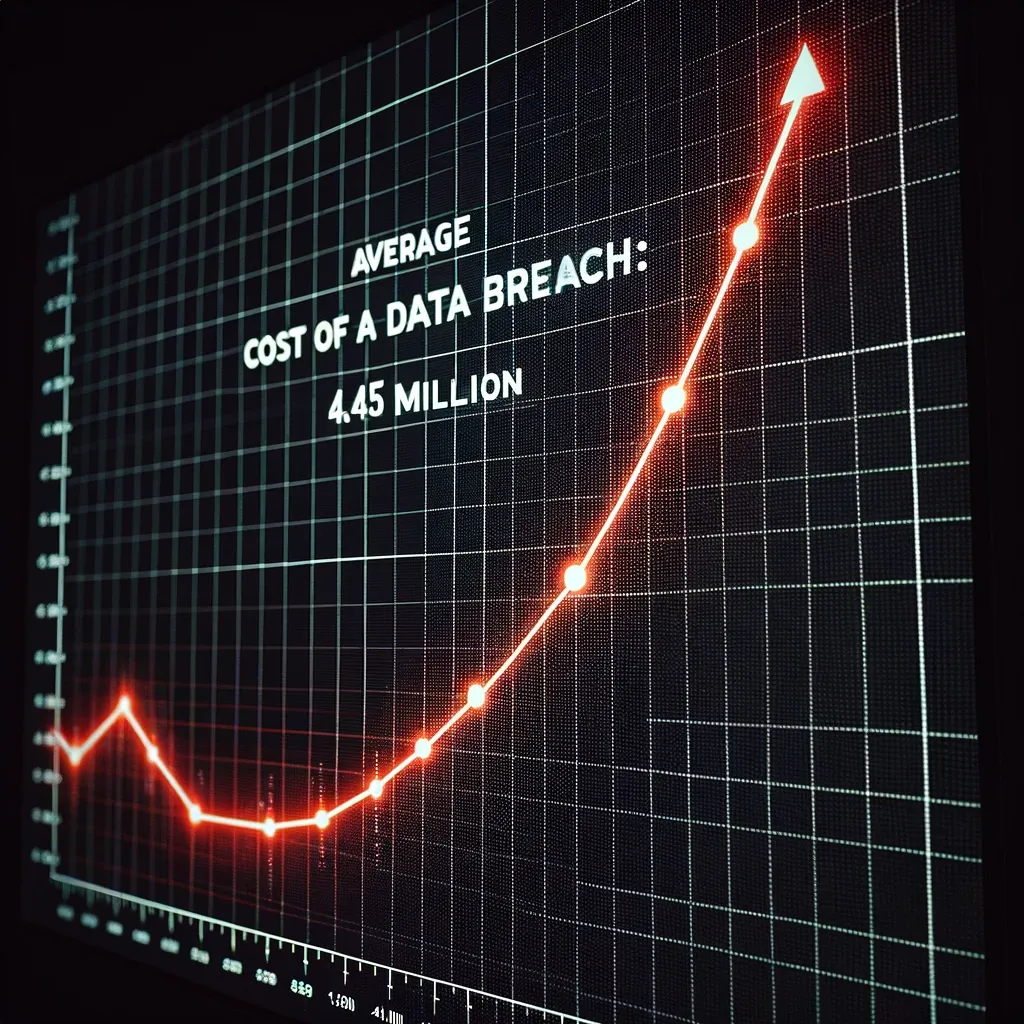
The global average cost of a data breach in 2023 was $4.45 million, a 15% increase over 3 years. According to IBM's Data Breach Reports.
What Costs Can it Cover?
*Please note that policies vary by provider and plan.
Customer Notifications. The expenses associated with notifying customers of a data breach.
Data and Identity Recovery. Restoring the personal identities of affected customers and costs to replace, restore, or repair damaged or destroyed data/software.
Ransom Demands. Most ransomware attacks involve a fee to retrieve compromised data. Insurance can help with the extortion demands and payments.
Remediation. Help with legal fees incurred through the violation of privacy policies and regulations, and the hiring of a computer forensic expert who can remediate the attack or recover compromised data.
Legal Counsel. Costs of hiring legal counsel to ensure organizations are complying with legal requirements and taking the correct steps following a breach or cyberattack.
Why Prevention is Key
Reputational Damage
Insurance may cover money lost but can't repair reputational damage.
Operational Downtime
Your operations may come to a halt due to a cyber attack which can cause service interruptions that insurance cannot mitigate.
Data Loss
Insurance cannot recover data that has been lost or compromised.
Insurance Limitations
Cyber insurance policies may contain exclusions or restrictions and might not cover financial losses sustained from every type of cyber-attack.
Not only has the average weekly number of attacks per organization worldwide reached over 1,130, a 28% increase compared to 2021…
CMMC is about an organizational culture of cybersecurity. Setting up systems, processes, and procedures that meet the DoD standards isn’t something that you can put together overnight.
However, with something as serious as cybersecurity…
Failure is not an option if you want to continue to maximize growth and even stay in business.
If you want to pass your CMMC assessment with flying colors you have two options:

Preventative Measures to Implement

Employee Training
Regularly educating staff on cybersecurity to help them identify and counter threats.
Multi-Factor Authentication
Incorporate MFA to enable additional layers of security to access sensitive data. *required by all insurance companies
Regular Updates and Patching
Update all systems, programs, and applications. Many updates patch vulnerabilities.
Firewalls and Antivirus Software
Invest in reliable security software and hardware to protect against various cyber threats.
Incident Response Plan
Create and implement an IRP for dealing with security breaches.
Typical Cyber Insurance Requirements:
Multi-Factor Authentication
Email & Web Filtering
Secure Backup
Patch & Vulnerability Management
Endpoint Detection and Response
Privileged Access Management
Cyber Incident Response Planning/Testing
Cybersecurity Awareness Training
System/Network Hardening/Protection
Logging and Monitoring
Vendor Supply Chain Management
End-of-Life System Upgrade Plans
How Can Stealth-ISS Reduce your Risk?
Aside from helping you with all of the requirements above, please ask yourself:
Do you know what data is at risk, and what it's worth per asset?
Do you know how attackers could access your unprotected data?
Do you know precisely where your data is located and who has access to it?
With our Data Risk Intelligence service, we can do the following:
Scan for unsecured data across your network and provide an estimated financial figure for your organization's potential liability in the event of a breach.
Identify any type of data, from Social Security numbers to driver's license numbers, bank accounts, and intellectual property.
Discover vulnerabilities by vendor and assess the severity level of each. This helps us identify which vulnerabilities should be addressed first.
Show you where the sensitive data is lurking and who has access to it.
We are able to identify exactly what data is putting your business at risk and prioritize the efforts and tasks to immediately reduce the impact this data could have on your business.
Cyber Insurance MAY help with financial loss BUT
CAN'T help with protection.
The best form of protection is ALWAYS prevention! In fact, some insurers may decline you cyber insurance if you don't have any of these.
Want to know more about cyber insurance requirements and the application process? Download our Navigating the Cyber Insurance Application Process here:
Secure Your Business Beyond Insurance.
Claim Your Complimentary Cyber Insurance Risk Evaluation Today!